Share via

Black Friday is coming. The countdown is on, and while retailers are gearing up for the biggest sales event of the year, cybercriminals are also getting ready for their own version of a holiday bonanza. If you run an eCommerce site, it’s not just about offering irresistible deals—it’s also about making sure your security measures are rock solid. This year, there’s one particular acronym you should get very familiar with: PCI DSS 4.x.
Why? Because protecting your customers’ data isn’t optional, especially when the stakes are this high.
Why does PCI DSS matter so much? In the simplest terms, it’s a set of stringent security standards that safeguard credit card information during online transactions. And with cyber threats evolving at breakneck speed, PCI DSS 4.x steps up the game, mandating a comprehensive approach to payment security that covers every touchpoint—from the payment form to the hosting web environment.
The message is clear: protecting your eCommerce site isn’t just about safeguarding your reputation. It’s about staying compliant and avoiding costly breaches that can devastate your business. Here’s how to get started.
Your Black Friday Security Checklist
As the digital battlefield intensifies around Black Friday, eCommerce sites must be armed to the teeth. These security practices apply to everyone, regardless of your platform:
- Strong Passwords and Two-Factor Authentication (2FA)
Let’s start with the basics. Weak passwords are an open invitation to hackers, so make yours as complex as possible. Use unique combinations, and don’t be shy about layering on two-factor authentication. Think of it as an extra security gate—a code from your phone or device that makes hacking significantly harder.
- Stay Current with Updates
Think of updates as digital armor. They patch vulnerabilities and keep your site secure. Outdated software, plugins, or extensions are playgrounds for hackers, so make regular updates a non-negotiable part of your routine.
- Choose a Secure Hosting Provider
Your hosting provider is your first line of defense. Opt for one that prioritises security, offering features like firewalls, intrusion detection, and routine backups. The difference between a secure host and a cut-rate one could be your entire business.
- SSL Certificates Are Non-Negotiable
SSL encryption isn’t just a nice-to-have; it’s essential. That little padlock icon next to your URL? It protects data like credit card information from being intercepted. If you don’t have one yet, stop everything and get it sorted.
- PCI DSS-Compliant Payment Gateways
This is where PCI DSS compliance becomes critical. Never attempt to store cardholder data on your own servers. Leave it to a PCI DSS-compliant payment gateway, which handles transactions securely and keeps you compliant with the latest standards.
What’s New with PCI DSS 4.x
Now that we’ve covered the essentials, let’s dig into what’s new with PCI DSS version 4.x. The latest update introduces future-dated requirements that become mandatory by March 2025, and these aren’t guidelines you can afford to ignore. Two of the most significant of the new and future-dated requirements include those outlined below.
Requirement 6.4.3: Inventory and Control of Payment Page Scripts
Requirement 6.4.3: Merchants must inventory all scripts running on payment pages and implement processes to detect and address unauthorized changes. It’s about stopping e-skimming in its tracks and ensuring hackers can’t slip rogue scripts onto your site.
- What it means: This requirement mandates that merchants must have a comprehensive inventory of all scripts running on their payment pages. This includes scripts that are loaded externally (e.g., from third-party providers) as well as any custom scripts. Additionally, merchants must implement processes to detect and address any unauthorized changes to these scripts.
- Why it matters: E-skimming attacks, where malicious scripts are injected into payment pages to steal card data, have become increasingly sophisticated. By maintaining a detailed script inventory and actively monitoring for changes, merchants can quickly identify and neutralize these threats, thus preventing data breaches.
Requirement 11.6.1: Regular Testing for Unauthorized Scripts
Requirement 11.6.1: You’ll need to regularly test for unauthorized scripts to catch any malicious activity aimed at intercepting payment data. This isn’t just an extra step; it’s an essential shield against digital theft.
- What it means: This requirement mandates regular testing for the presence of unauthorized scripts on payment pages. This testing must be performed at least quarterly or whenever significant changes are made to the payment environment.
- Why it matters: Even with robust change detection mechanisms, unauthorized scripts can sometimes slip through the cracks. Regular testing provides an additional layer of security by actively searching for any malicious scripts that may have been injected onto payment pages.
Remember: These are just two of the many new requirements introduced in PCI DSS 4.x. It’s crucial for merchants to familiarize themselves with the full standard and work with their payment service providers to ensure compliance.
Final Thoughts
Black Friday is a golden opportunity for your business—but also for cybercriminals. By implementing these best practices and staying ahead with PCI DSS 4.x, you can ensure that your eCommerce site isn’t just set up for sales success but fortified against the digital threats lurking in the shadows.
Remember, the future of your business is only as secure as the measures you take today. So, lock it down, get compliant, and make this Black Friday your safest—and most successful—yet.
Scale with Peach
Learn how we help scale some of Africa's most exciting businesses
Business tips, case studies, interviews with online store owners and business trends…
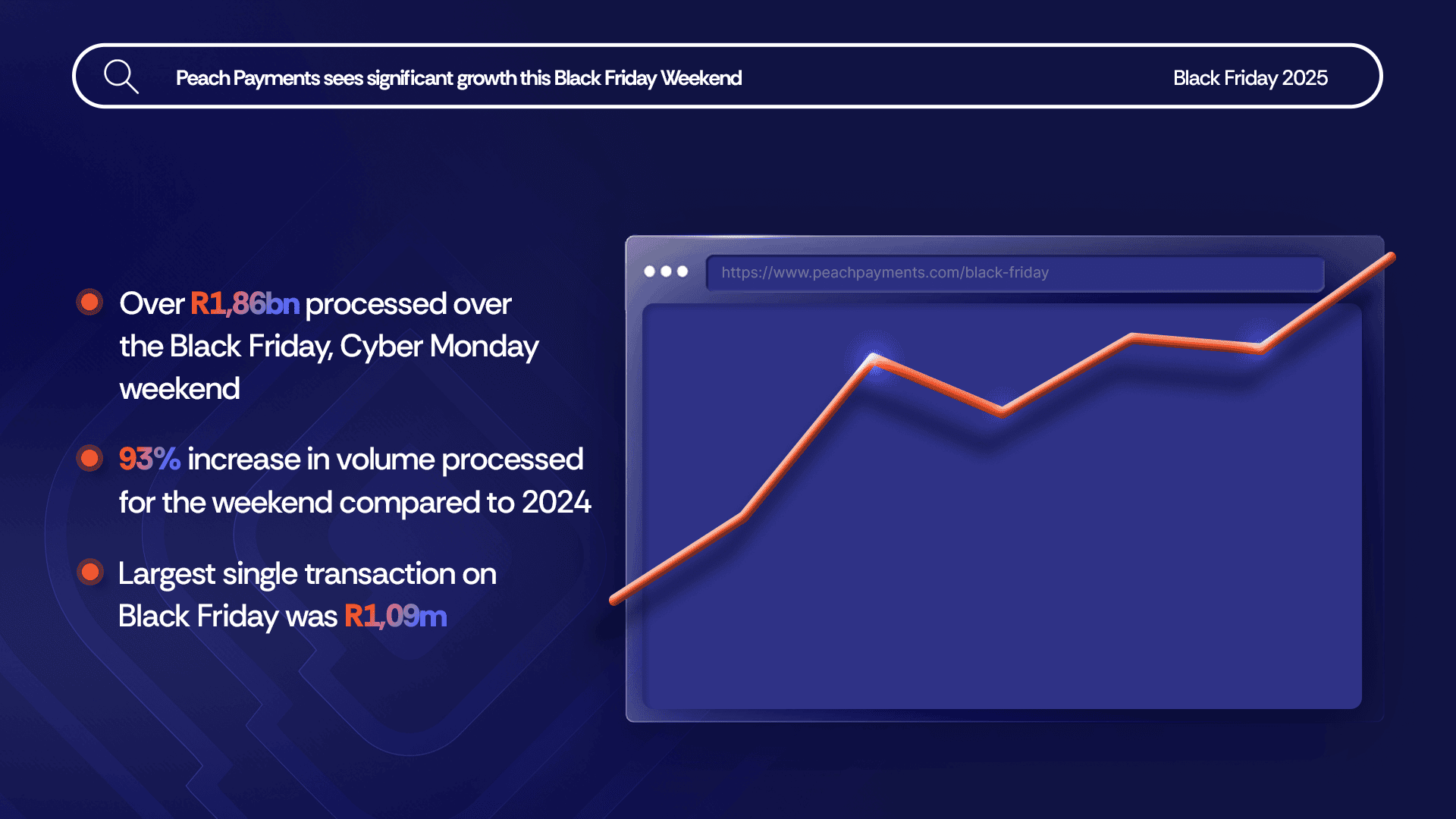
Black Friday up 93% over 2024, R1,86bn processed

Bringing Our New Peach Values to Life

Samsonite in-store payment methods
How global and regional companies can use the Mauritius IFC to centralise online payments and treasury functions

# PeachFriday Merchant Deals 2025
A merchant’s guide to chargebacks

Four Black Friday payment realities for merchants

What are Direct Merchant Accounts (ISO) versus Aggregation Accounts?

What Is 3RI? Everthing you need to know about Requestor-Initiated Authentication

Highlights from the 2025 World Wide Worx Online Retail Report

What is Interchange? Everything you need to know about interchange fees

Cadana Pay x Peach Payments: Unlocking seamless global Payouts

Peach Payments announces real-time clearance Payouts
Peach Payments x MoneyBadger partnership goes live

Peach Payments launches enterprise-level POS terminal

iTickets x Peach Payments Point of Sale

Peach Payments x Digicape: Powering Premium Apple Experiences with Seamless Payments

Peach Payments acquires West-African payments gateway PayDunya

Navigating International Transactions
Seize the Sale with Buy Now, Pay Later
2024 Wrapped: A Year of Innovation and Growth at Peach Payments
RCS payment option now available through Peach Payments

Peach Payments sees impressive growth this Black Friday Weekend

#PeachFriday Merchant Deals 2024

Your Ultimate Guide to Payment Security for Black Friday

Scaling with Peach Payments: Unveiling the Product Roadmap

Scaling with Peach Payments: Revolutionising Reconciliation

Scaling with Peach Payments: The Future of Payments

Scaling with Peach Payments: How Peach Payments is Keeping Your Business Safe

Scaling with Peach Payments: Insights from the Think Bigger Summit 2024




